In this blog post we will focus on the support for signing Windows executables with SignServer Enterprise using Authenticode, one of the most popular formats.
Digital Signatures and Central Code Signing
Whenever software is being distributed over the Internet (or
other insecure network), or it is stored on untrusted media, it is crucial to use a reliable signing tool to digitally sign all executable files
such as applications, libraries and drivers.
Harmful code is today a real threat to users and organizations
alike, as criminal groups and even governments use malicious software
to steal and monitor data, extort money or empty your bank
account.
Digitally signed code ensures that the transferred software
is trusted and unmodified. That is, as long as one picks a secure signing tool. Simply setting up any code
signing tool you are able to find, may result in an insecure solution that makes
you vulnerable to all sorts of attacks. PrimeKey's signing solution SignServer Enterprise, is proven and allows you to keep your code signing keys and certificates secure and audit ready.
Code signing is crucial for distributing code in many systems:
- Windows executable files, libraries, drivers and updates.
- Firmware for hardware devices.
- Mobile apps (Android, iOS)
- OS X apps, XCode.
- Java applications (Applets, WebStart, Oracle Java).
- Plugins and addons in man applications (Mozilla, Firefox, Thunderbird XPI, NetBeans modules etc).
- Software from repositories for Linux and Apple OS X.
Three good reasons to use Central Signing
Protection of Signing Keys
The primary reason to use a secure,
centralized code signing solution, is to keep code signing keys protected. For this purpose, keys are kept securely in a Hardware Security Module (HSM), mitigating the risk of any key being stolen or used illegitimately.
Centralized control
Many organizations have code signing keys and certificates spread out
in different departments and with different developers across the
organization. Keeping track of where the signature capabilities
reside, and who is allowed to sign code on the organization's behalf,
quickly becomes difficult or even unmanageable.
With the centralized signing
solution the code signing capabilities are easily controlled from a single location, and the risk of code
signing keys being lost or stolen is significantly decreased. The more
efficient handling lowers the costs and you may even escape from buying code signing
certificates for different people.
Policy and Audit compliance
An organization needs to be able to see exactly when, and for what, a particular code signing key (and its certificate) has been used, and there are usually strict
policies surrounding how code signing should be done.
Using a central code signing solution makes it easy to achieve and enforce a strict audit
record of who signed what. Some organizations demand this because of
external audit requirements. While others need it to maintain trust in
their brand, where maintaining good policy and audit records assure that
the users of their products are not exposed to unnecessary risks of malicious software.
Using SignServer for code signing
SignServer
is PrimeKey's code signing solution that helps you to keep secure control of
your code signing keys, and also provides a centrally managed and audited
single service for all your code signing needs.
SignServer lets different project members or systems authenticate and share the same
well protected code signing key and certificate when signing, and at the
same time provides audit records of who signed what. For that matter,
SignServer can also control individual code signing keys where only one
person is granted authorization.
SignServer Enterprise serves most code signing needs using different signers and custom plug-ins, and support for Authenticode was added from SignServer Enterprise 3.6.3. All you need to start signing code is a signature key pair, generated by SignServer, and a code signing certificate, issued by a private CA such as
EJBCA or a public CA.
Windows' Authenticode for executable files
Microsoft has specified a format for digital signatures in software binaries
called Authenticode. Using Authenticode, the signature is embedded within some type of
portable executable (PE) file, typically with file endings like .exe, .dll, .sys and .ocx.
In Windows, after an executable file has been downloaded and is about to
be run, a security warning dialog box will appear (see picture below). At this moment the
embedded signature has been verified, the code signing certificate has
been verified that it was issued by a trusted CA, and the name of the
publisher is displayed to the user. The dialog box asks the user to
confirm if it is ok to start the application created by that
publisher:
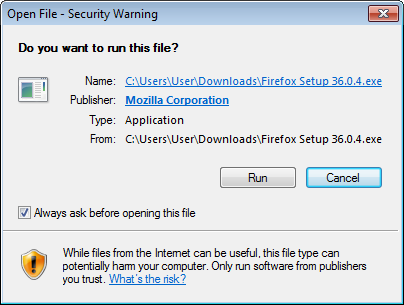 |
| Do you want to run this file? Publisher: Mozilla Corporation |
If the file had not been signed, a different warning would be displayed, asking the
user to confirm that the software should be run, even if the
publisher is not known:
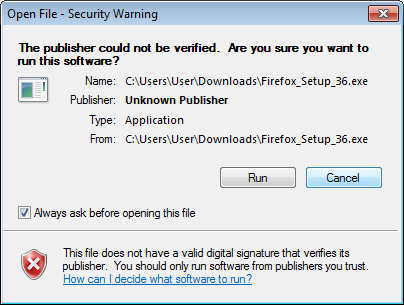 |
| The publisher could not be verified. Are you sure you want to run this software? |
Authenticode in SignServer
Since SignServer Enterprise 3.6.3, there is an Authenticode signer for PE files.
The signer is configured just like any
other signer in SignServer. The only special requirement for this signer is to use a code signing certificate.
If your organization already has a CA (for example EJBCA) configured to be trusted by your users, you can use that CA to issue
the certificate. Otherwise you could buy a certificate from one of the
CAs already trusted by default in Windows.
For testing purposes, and also for test environments in general, you could issue the
certificate yourself. Just remember to have the extended key usage
“Code Signing” set and that you have to install the CA certificate in
your test environment.
You need to install the CA certificate in
your test environment and remember to have the extended key usage
set to “Code Signing”.
In addition there are a few configuration options that can be
applied to specify additional attributes, such as: the name of the
application, if time stamping should be used, which service to use etc.
Details of configuration options are documented in the
SignServer Manual.
After configuring and activating the signer, a user can sign code, for example by using the
Generic Signing page, specifying the name of the signer and providing the binary to upload:
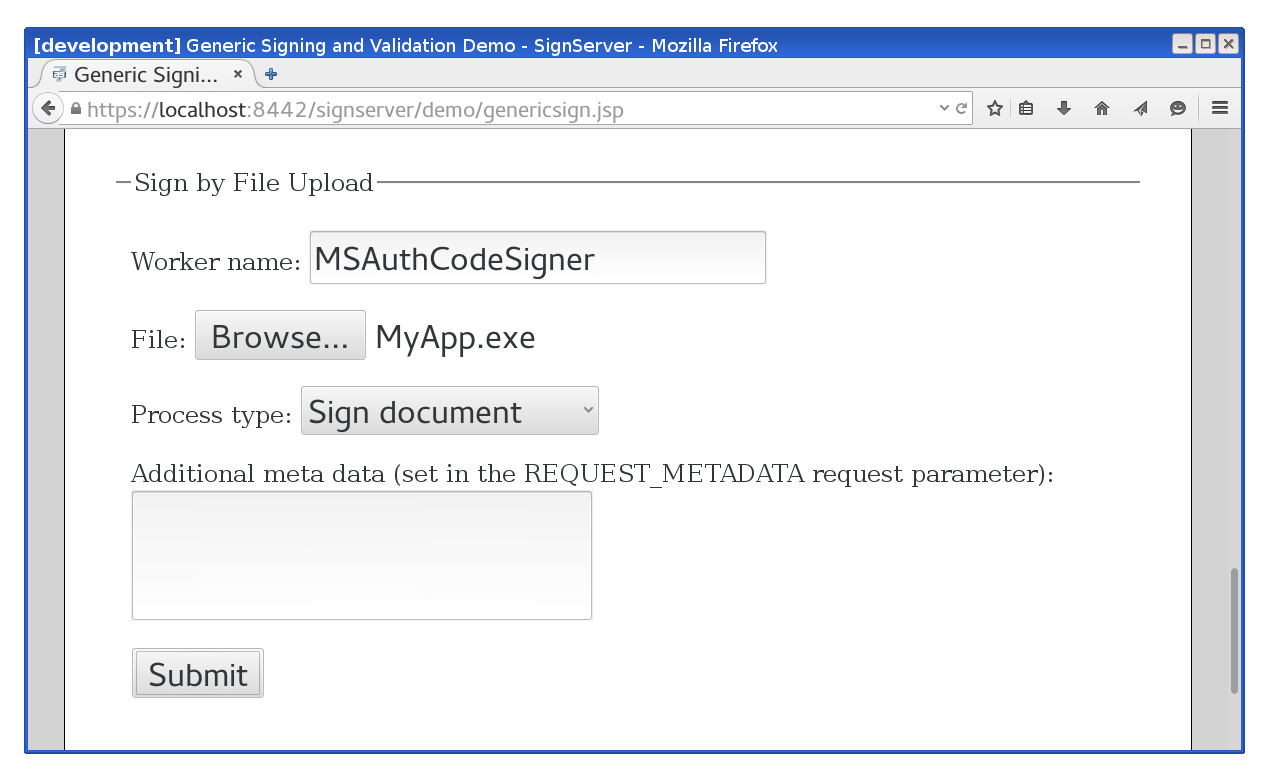 |
| Signer upload form |
After submitting the file, the signed version (with the embedded signature) is returned:
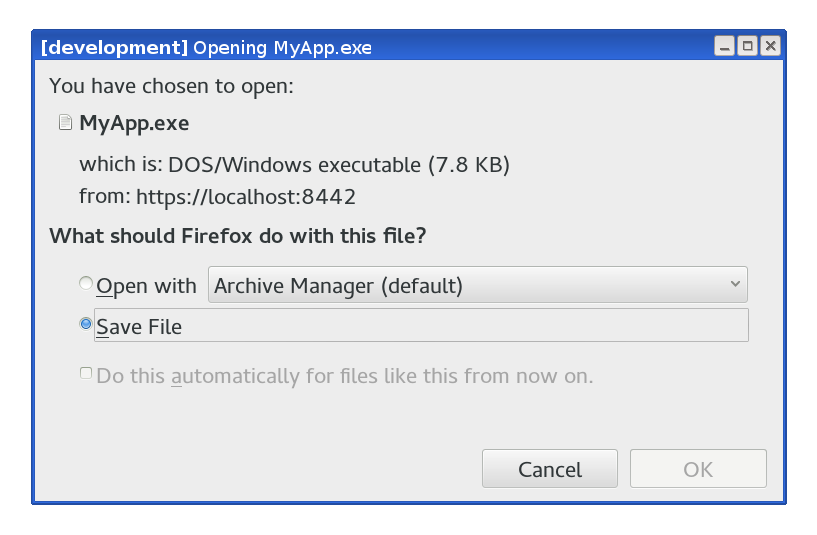 |
| Save signed file |
In Windows, the signature attached to a specific file can be manually inspected:
- Right click on the file and choose Properties.
- Click on the Digital Signatures tab.
- Select the signature in the Signatures list and click Details.
|
|
Displaying the signature details on an executable file
|
Integration
You can use other
interfaces of SignServer (such as the
web service interface) to integrate code signing with other systems and applications in a completely transparent way.
More information
Basic information on
SignServer Enterprise and PrimeKey
Code Signing Appliance is available at PrimeKey.









No comments:
Post a Comment